-->
Delete Key Issue In Outlook I have been having an issue where I review an email in my inbox by reading it in the preview pane. After reading I hit 'delete' and it seems like the key gets stuck and starts going down my inbox rapidly deleting every email until I hit the escape key.
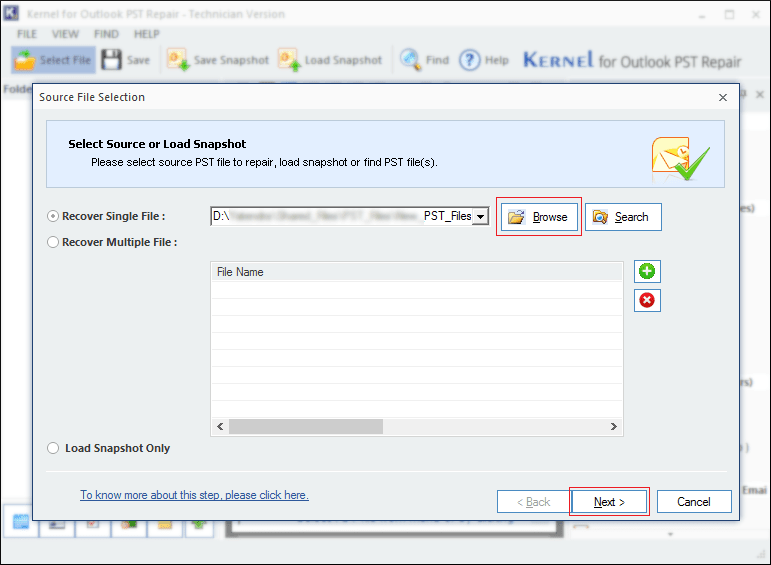
- By clicking on the Next button, you go on directly to the backup operation: Backup Outlook Basic creates a self-extracting archive with backup copies of your e-mail, the Outlook address book and settings (PST files). Upon completion of the backup process, the tool shows the following window.
- Backup Outlook 4 0 Key On Keyboard Download Eyeshield 21 Sub Indo Mkv Lengkap Panduan Gratis Plants Vs Zombies 2 Full Version Untuk Pcc Misale Ya Waumini Online.
This article describes the app protection policy settings for iOS/iPadOS devices. The policy settings that are described can be configured for an app protection policy on the Settings pane in the portal when you make a new policy.
There are three categories of policy settings: Data relocation, Access requirements, and Conditional launch. In this article, the term policy-managed apps refers to apps that are configured with app protection policies.

Important
The Intune Managed Browser has been retired. Use Microsoft Edge for your protected Intune browser experience.
Data protection
Data Transfer
| Setting | How to use | Default value |
|---|---|---|
| Backup Org data to iTunes and iCloud backups | Select Block to prevent this app from backing up work or school data to iTunes and iCloud. Select Allow to allow this app to back up of work or school data to iTunes and iCloud. | Allow |
| Send Org data to other apps | Specify what apps can receive data from this app:
In addition, when set to Policy managed apps or None, the Spotlight search (enables searching data within apps) and Siri shortcuts iOS features are blocked. This policy can also apply to iOS/iPadOS Universal Links. General web links are managed by the Open app links in Intune Managed Browser policy setting. There are some exempt apps and services to which Intune may allow data transfer by default. In addition, you can create your own exemptions if you need to allow data to transfer to an app that doesn't support Intune APP. See data transfer exemptions for more information. | All apps |
| This option is available when you select Policy managed apps for the previous option. | |
| Choose Block to disable the use of the Save As option in this app. Choose Allow if you want to allow the use of Save As. When set to Block, you can configure the setting Allow user to save copies to selected services. Note:
| Allow |
| Users can save to the selected services (OneDrive for Business, SharePoint, and Local Storage). All other services are blocked. OneDrive for Business: you can save files to OneDrive for Business and SharePoint Online. SharePoint: you can save files to on-premises SharePoint. Local Storage: you can save files to local storage. | 0 selected |
| Typically, when a user selects a hyperlinked phone number in an app, a dialer app will open with the phone number prepopulated and ready to call. For this setting, choose how to handle this type of content transfer when it is initiated from a policy-managed app:
Note: This setting requires Intune SDK 12.7.0 and later. If your apps rely on dialer functionality and are not using the correct Intune SDK version, as a workaround, consider adding 'tel;telprompt' as a data transfer exemption. Once the apps support the correct Intune SDK version, the exemption can be removed. | Any dialer app |
| When a specific dialer app has been selected, you must provide the dialer app URL scheme that is used to launch the dialer app on iOS devices. For more information, see Apple's documentation about Phone Links. | Blank |
| Receive data from other apps | Specify what apps can transfer data to this app:
| All apps |
| Select Block to disable the use of the Open option or other options to share data between accounts in this app. Select Allow if you want to allow the use of Open. When set to Block you can configure the Allow user to open data from selected services to specific which services are allowed for Org data locations. Note:
| Allow |
| Select the application storage services that users can open data from. All other services are blocked. Selecting no services will prevent users from opening data from external locations. Supported services:
| All selected |
| Restrict cut, copy and paste between other apps | Specify when cut, copy, and paste actions can be used with this app. Select from:
| Any app |
| Specify the number of characters that may be cut or copied from Org data and accounts. This will allow sharing of the specified number of characters to any application, regardless of the Restrict cut, copy, and paste with other apps setting. Default Value = 0 Note: Requires app to have Intune SDK version 9.0.14 or later. | 0 |
| Third party keyboards | Choose Block to prevent the use of third-party keyboards in managed applications. When this setting is enabled, the user receives a one-time message stating that the use of third-party keyboards is blocked. This message appears the first time a user interacts with organizational data that requires the use of a keyboard. Only the standard iOS/iPadOS keyboard is available while using managed applications, and all other keyboard options are disabled. This setting will affect both the organization and personal accounts of multi-identity applications. This setting does not affect the use of third-party keyboards in unmanaged applications. Note: This feature requires the app to use Intune SDK version 12.0.16 or later. Apps with SDK versions from 8.0.14 to, and including, 12.0.15, will not have this feature correctly apply for multi-identity apps. For more details, see Known issue: Third party keyboards are not blocked in iOS/iPadOS for personal accounts. | Allow |
Encryption
| Setting | How to use | Default value |
|---|---|---|
| Encrypt Org data | Choose Require to enable encryption of work or school data in this app. Intune enforces iOS/iPadOS device-level encryption to protect app data while the device is locked. In addition, applications may optionally encrypt app data using Intune APP SDK encryption. Intune APP SDK uses iOS/iPadOS cryptography methods to apply 256-bit AES encryption to app data. When you enable this setting, the user may be required to set up and use a device PIN to access their device. If there's no device PIN and encryption is required, the user is prompted to set a PIN with the message 'Your organization has required you to first enable a device PIN to access this app.' Go to the official Apple documentation to see which iOS/iPadOS encryption modules are FIPS 140-2 validated. | Require |
Functionality
| Setting | How to use | Default value |
|---|---|---|
| Sync policy managed app data with native apps | Choose Block to prevent the policy managed apps from saving data to the native Contacts app on the device. If you choose Allow, the app can save data to the native Contacts app on the device, when those features are enabled within the policy managed app. When you perform a selective wipe to remove work, or school data from the app, contacts data synced directly from the app to the native Contacts app are removed. Any contacts data synced from the native Contacts app to another external source can't be wiped. Currently, this applies only to Outlook for iOS app; for more information, see Deploying Outlook for iOS and Android app configuration settings. | Allow |
| Printing Org data | Select Block to prevent the app from printing work or school data. If you leave this setting to Allow, the default value, users will be able to export and print all Org data. | Allow |
| Restrict web content transfer with other apps | Specify how web content (http/https links) are opened from policy-managed applications. Choose from:
If a policy-managed browser is required but not installed, your end users will be prompted to install the Microsoft Edge. If a policy-managed browser is required, iOS/iPadOS Universal Links are managed by the Allow app to transfer data to other apps policy setting. Intune device enrollment Policy-managed Microsoft Edge
Note:The Intune SDK cannot determine if a target app is a browser. On iOS/iPadOS devices, no other managed browser apps are allowed. | Not configured |
| Enter the protocol for a single unmanaged browser. Web content (http/https links) from policy managed applications will open in any app that supports this protocol. The web content will be unmanaged in the target browser. This feature should only be used if you want to share protected content with a specific browser that is not enabled using Intune app protection policies. You must contact your browser vendor to determine the protocol supported by your desired browser. Note: Include only the protocol prefix. If your browser requires links of the form mybrowser://www.microsoft.com, enter mybrowser.Links will be translated as:
| Blank |
| Org data notifications | Specify how Org data is shared via OS notifications for Org accounts. This policy setting will impact the local device and any connected devices such as wearables and smart speakers. Apps may provide additional controls to customize notification behavior or may choose to not honor all values. Select from:
Note: This setting requires app support:
| Allow |
Note
None of the data protection settings control the Apple managed open-in feature on iOS/iPadOS devices. To use manage Apple open-in, see Manage data transfer between iOS/iPadOS apps with Microsoft Intune.
Data transfer exemptions
There are some exempt apps and platform services that Intune app protection policy may allow data transfer to and from in certain scenarios. This list is subject to change and reflects the services and apps considered useful for secure productivity.
Third party unmanaged apps can be added to the exemptions list which can allow data transfer exceptions. For additional details and examples, see How to create exceptions to the Intune App Protection Policy (APP) data transfer policy. The exempt unmanaged app must be invoked based on iOS URL protocol. For example, when data transfer exemption is added for an unmanaged app, it would still prevent users from cut, copy, and paste operations, if restricted by policy. This type of exemption would also prevent users from using Open-in action within a managed app to copy data to exempt app since it is not based on iOS URL protocol. For more information about Open-in, see Use app protection with iOS apps.
| App/service name(s) | Description |
|---|---|
skype | Skype |
app-settings | Device settings |
itms; itmss; itms-apps; itms-appss; itms-services | App Store |
calshow | Native Calendar |
Important
4 Divided By 0 Equals
App Protection policies created before June 15, 2020 include tel and telprompt URL scheme as part of the default data transfer exemptions. These URL schemes allow managed apps to initiate the dialer. The App Protection policy setting Transfer telecommunication data to has replaced this functionality. Administrators should remove tel;telprompt; from the data transfer exemptions and rely on the App Protection policy setting, provided the managed apps that initiate dialer functionality include the Intune SDK 12.7.0 or later.
Important
Backup Outlook 4 0 Key On Keyboard Windows 10
In Intune SDK 14.5.0 or later, including sms and mailto URL schemes in the data transfer exemptions will also allow sharing of Org data to the MFMessageCompose (for sms) and MFMailCompose (for mailto) view controllers within policy managed applications.
Access requirements
| Setting | How to use | Default value |
|---|---|---|
| PIN for access | Select Require to require a PIN to use this app. The user is prompted to set up this PIN the first time they run the app in a work or school context. The PIN is applied when working either online or offline. You can configure the PIN strength using the settings available under the PIN for access section. | Require |
| Set a requirement for either numeric or passcode type PINs before accessing an app that has app protection policies applied. Numeric requirements involve only numbers, while a passcode can be defined with at least 1 alphabetical letter or at least 1 special character. Note:To configure passcode type, it requires app to have Intune SDK version 7.1.12 or above. Numeric type has no Intune SDK version restriction. Special characters allowed include the special characters and symbols on the iOS/iPadOS English language keyboard. | Numeric |
| Select Allow to allow users to use simple PIN sequences like 1234, 1111, abcd or aaaa. Select Block to prevent them from using simple sequences. Simple sequences are checked in 3 character sliding windows. If Block is configured, 1235 or 1112 would not be accepted as PIN set by the end user, but 1122 would be allowed. Note: If Passcode type PIN is configured, and Allow simple PIN is set to Yes, the user needs at least 1 letter or at least 1 special character in their PIN. If Passcode type PIN is configured, and Allow simple PIN is set to No, the user needs at least 1 number and 1 letter and at least 1 special character in their PIN. | Allow |
| Specify the minimum number of digits in a PIN sequence. | 4 |
| Select Allow to allow the user to use Touch ID instead of a PIN for app access. | Allow |
| To use this setting, select Require and then configure an inactivity timeout. | Require |
| Specify a time in minutes after which either a passcode or numeric (as configured) PIN will override the use of a fingerprint or face as method of access. This timeout value should be greater than the value specified under 'Recheck the access requirements after (minutes of inactivity)'. | 30 |
| Select Allow to allow the user to use facial recognition technology to authenticate users on iOS/iPadOS devices. If allowed, Face ID must be used to access the app on a Face ID capable device. | Allow |
| Select Yes to require users to change their app PIN after a set period of time, in days. When set to Yes, you then configure the number of days before the PIN reset is required. | No |
| Configure the number of days before the PIN reset is required. | 90 |
| Select Disable to disable the app PIN when a device lock is detected on an enrolled device with Company Portal configured. Note:Requires app to have Intune SDK version 7.0.1 or above. On iOS/iPadOS devices, you can let the user prove their identity by using Touch ID or Face ID instead of a PIN. Intune uses the LocalAuthentication API to authenticate users using Touch ID and Face ID. To learn more about Touch ID and Face ID, see the iOS Security Guide. When the user tries use this app with their work or school account, they're prompted to provide their fingerprint identity or face identity instead of entering a PIN. When this setting is enabled, the App-switcher preview image will be blurred while using a work or school account. | Enable |
| Work or school account credentials for access | Select Require to require the user to sign in with their work or school account instead of entering a PIN for app access. If you set this to Require, and PIN or biometric prompts are turned on, both corporate credentials and either the PIN or biometric prompts are shown. | Not required |
| Recheck the access requirements after (minutes of inactivity) | Configure the number of minutes of inactivity that must pass before the app requires the user to again specify the access requirements. For example, an admin turns on PIN and Blocks rooted devices in the policy, a user opens an Intune-managed app, must enter a PIN, and must be using the app on a non-rooted device. When using this setting, the user would not have to enter a PIN or undergo another root-detection check on any Intune-managed app for a period of time equal to the configured value. Note:On iOS/iPadOS, the PIN is shared amongst all Intune-managed apps of the same publisher. The PIN timer for a specific PIN is reset once the app leaves the foreground on the device. The user wouldn't have to enter a PIN on any Intune-managed app that shares its PIN for the duration of the timeout defined in this setting. This policy setting format supports a positive whole number. | 30 |
Note
To learn more about how multiple Intune app protection settings configured in the Access section to the same set of apps and users work on iOS/iPadOS, see Intune MAM frequently asked questions and Selectively wipe data using app protection policy access actions in Intune.
Conditional launch
Configure conditional launch settings to set sign-in security requirements for your access protection policy.
By default, several settings are provided with pre-configured values and actions. You can delete some of these, like the Min OS version. You can also select additional settings from the Select one dropdown.
| Setting | How to use |
|---|---|
| Max OS version | Specify a maximum iOS/iPadOS operating system to use this app. Actions include:
This entry can appear multiple times, with each instance supporting a different action. This policy setting format supports either major.minor, major.minor.build, major.minor.build.revision. Note:Requires app to have Intune SDK version 14.4.0 or above. |
| Min OS version | Specify a minimum iOS/iPadOS operating system to use this app. Actions include:
This policy setting format supports either major.minor, major.minor.build, major.minor.build.revision. Note:Requires app to have Intune SDK version 7.0.1 or above. |
| Max PIN attempts | Specify the number of tries the user has to successfully enter their PIN before the configured action is taken. If the user fails to successfully enter their PIN after the maximum PIN attempts, the user must reset their pin after successfully logging into their account and completing a Multi-Factor authentication (MFA) challenge if required. This policy setting format supports a positive whole number. Actions include:
|
| Offline grace period | The number of minutes that policy-managed apps can run offline. Specify the time (in minutes) before the access requirements for the app are rechecked. Actions include:
|
| Jailbroken/rooted devices | There is no value to set for this setting. Actions include:
|
| Disabled account | There is no value to set for this setting. Actions include:
|
| Min app version | Specify a value for the minimum application version value. Actions include:
This entry can appear multiple times, with each instance supporting a different action. This policy setting format supports either major.minor, major.minor.build, major.minor.build.revision. Note:Requires app to have Intune SDK version 7.0.1 or above. Additionally, you can configure where your end users can get an updated version of a line-of-business (LOB) app. End users will see this in the min app version conditional launch dialog, which will prompt end users to update to a minimum version of the LOB app. On iOS/iPadOS, this feature requires the app to be integrated (or wrapped using the wrapping tool) with the Intune SDK for iOS v. 10.0.7 or above. To configure where an end user should update a LOB app, the app needs a managed app configuration policy sent to it with the key, com.microsoft.intune.myappstore. The value sent will define which store the end user will download the app from. If the app is deployed via the Company Portal, the value must be CompanyPortal. For any other store, you must enter a complete URL. |
| Min SDK version | Specify a minimum value for the Intune SDK version. Actions include:
This entry can appear multiple times, with each instance supporting a different action. |
| Device model(s) | Specify a semi-colon separated list of model identifier(s). These values are not case sensitive. Actions include:
|
| Max allowed device threat level | App protection policies can take advantage of the Intune-MTD connector. Specify a maximum threat level acceptable to use this app. Threats are determined by your chosen Mobile Threat Defense (MTD) vendor app on the end user device. Specify either Secured, Low, Medium, or High. Secured requires no threats on the device and is the most restrictive configurable value, while High essentially requires an active Intune-to-MTD connection. Actions include:
For more information on using this setting, see Enable MTD for unenrolled devices. |
Learn more
- Learn about LinkedIn information and features in your Microsoft apps.
- Learn about LinkedIn account connections release on the Microsoft 365 Roadmap page.
- Learn about Configuring LinkedIn account connections.
- For more information about data that is shared between users' LinkedIn and Microsoft work or school accounts, see LinkedIn in Microsoft applications at your work or school.
In the days of desktop calendars it was quite usual to have a calendar permanently on display. This not only made it quick and easy to enter new appointments when necessary, but also to check what was happening in the days and weeks ahead. With the move to digital calendars such as Outlook, it is easy to lose your calendar under a sea of windows. This is something that Outlook on the Desktop aims to address, ensuring that your Outlook calendar is never too far away.
As you’ve probably guessed from the name, this is a program that adds your Outlook calendar directly to the desktop. This means that when you need to check what is planned for the week ahead, all you need to do is press the Windows key and M to minimize all open windows and you’ll be able to see in a flash. All you need is a copy of Outlook 2003 or later and you’re good to go.
The benefit of using this app rather than sticking with working with Outlook in the more traditional way is that while your calendar can still get buried, getting it back it just a keyboard shortcut away. To prevent the calendar from being too distracting if you are the sort of person that makes extensive use of the desktop for other things, the opacity of the app can be adjusted to give a slightly more faded and subtle look.
Outlook on the Desktop really does provide you with a complete, customizable Outlook window integrated into the desktop. As such, anything you can do in Outlook, you are now able to achieve from the desktop. You are not restricted to viewing the calendar; you can also switch to your inbox, contacts and other sections of the app. There is support for drag and drop, and a system tray icon provides access to even more options.
Verdict:
A great way to access Outlook without the need to constantly switch windows – a real time saving tool.